Using Pihole to fight phishing

Introduction
Due to recent events about COVID-19 some Health Centers in Europe are victims of ramsonware attacks. The first channel to spread ransomware is phishing so here are some suggestion to block surfing to phishing sites if you have clicked on the phishing link in the email. I installed some time ago the Pihole Ad Blocking on my Raspberry Pi, to avoid the annoiyng commercials AD when surfing the net from home. But the Pihole can have more powerful applications such as adding other types of blacklist to the Pihole - and phishing site black list could be one of them.
The chain
The chain to follow to transform your Pihole in a DNS that blocks phishing links is preatty easy:
- download and install the Pihole; there are many guides in Internet, depending on where you want to install it here’s one for Raspberry
- add the phishing list to the
adlist.listof your Pihole istallation - update your Gravity list
- report and vote for phishing sites
- check that pihole blocks DNS queries
As said, the first step is pretty simple - yet it’s offtopic here (ping me if you are in trouble with the installation), so I’ll discuss directly the second point.
Add phishing list
I recently found a very good project that updates a phishing blacklist every 6 hours. This list could be implemented in the Pihole to block phishing sites. It is called Phishing Army and it updates its lists directly from 3 sources:
Add Phishing Army blacklist to your Pihole
To add the Phishing Army black list to your Pihole simply add the list to the list file in the path /etc/pihole/adlist.list file in your Pihole installation.
Just connect to the Pihole via ssh and type this command
# vim /etc/pihole/adlists.list
paste the link at the bottom of your list file, write and quit.
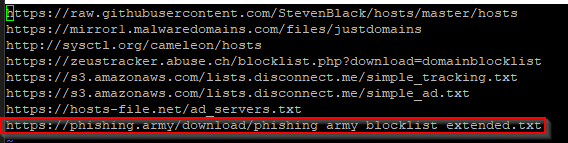
Update your Gravity list
Now you have to update the Gravity black list by typing the command
# pihole -g
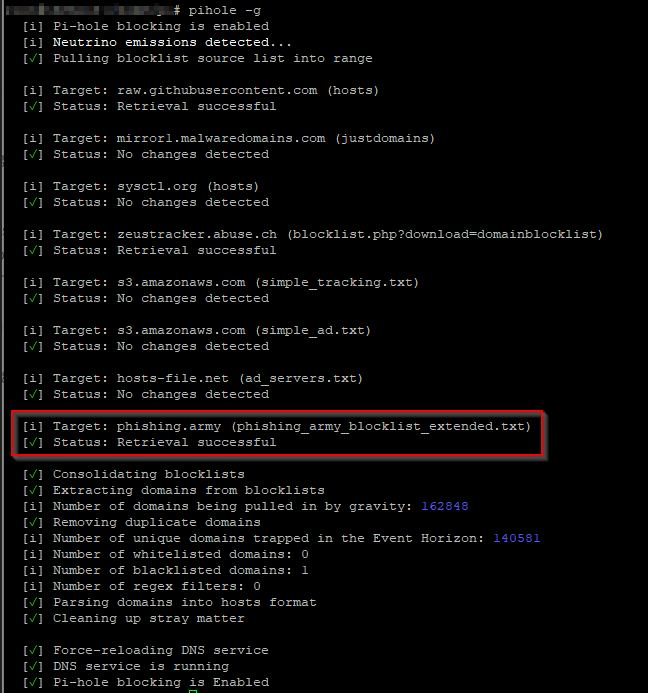
Report and vote for phishing sites
The first thing to do is to report and vote for phishing sites, the easy way is to follow the instruction written on the amazing blog of the CyberV19 volunteers about voting system on Phishtank. When the link reaches a good number of votes it is marked as phishing, then it will be put in the blacklist update of Phishing Army and automatically inside your Pihole.
Checks
Now you can check if your Pihole is blocking malicious DNS requests. Search for a full or partial link in the Query Lists Search of the Pihole
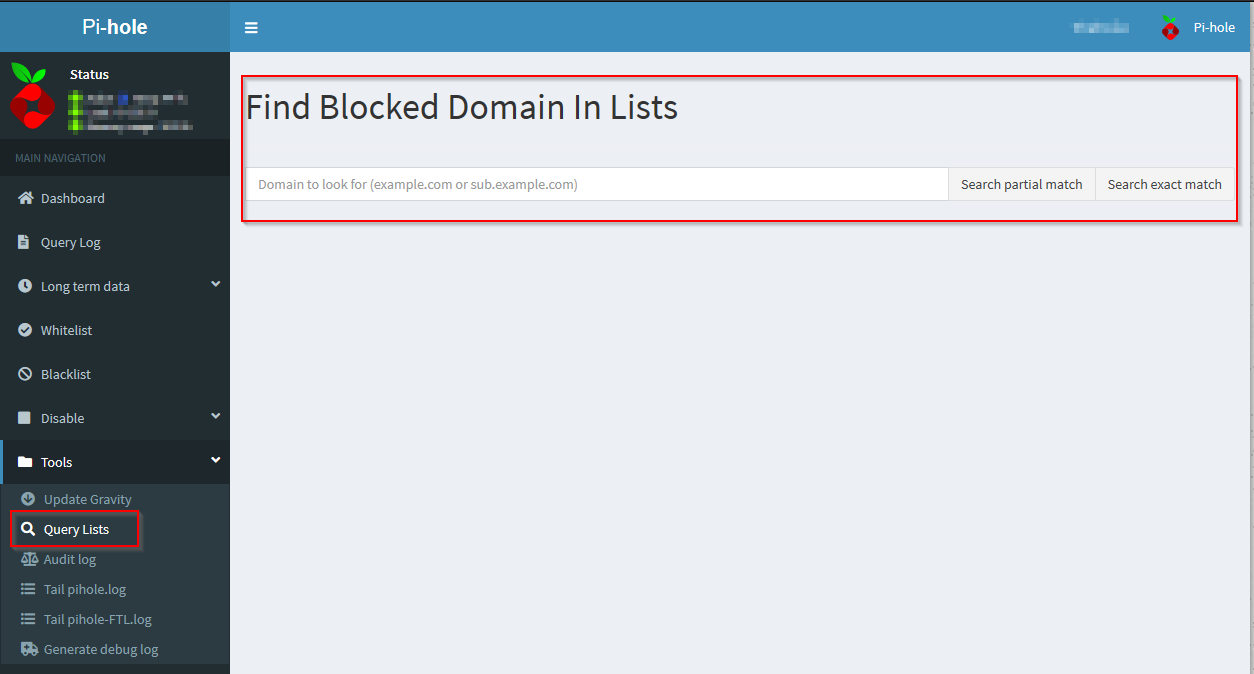
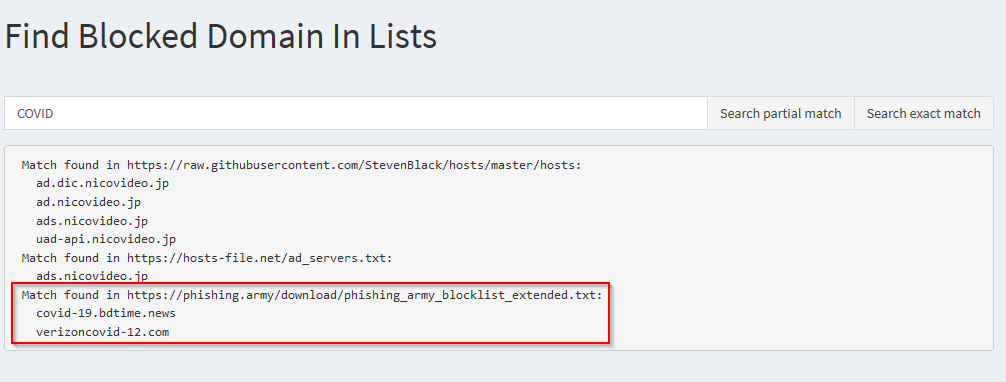
Try to surf one of the links in the results and see the DNS query blocked by the Pihole.
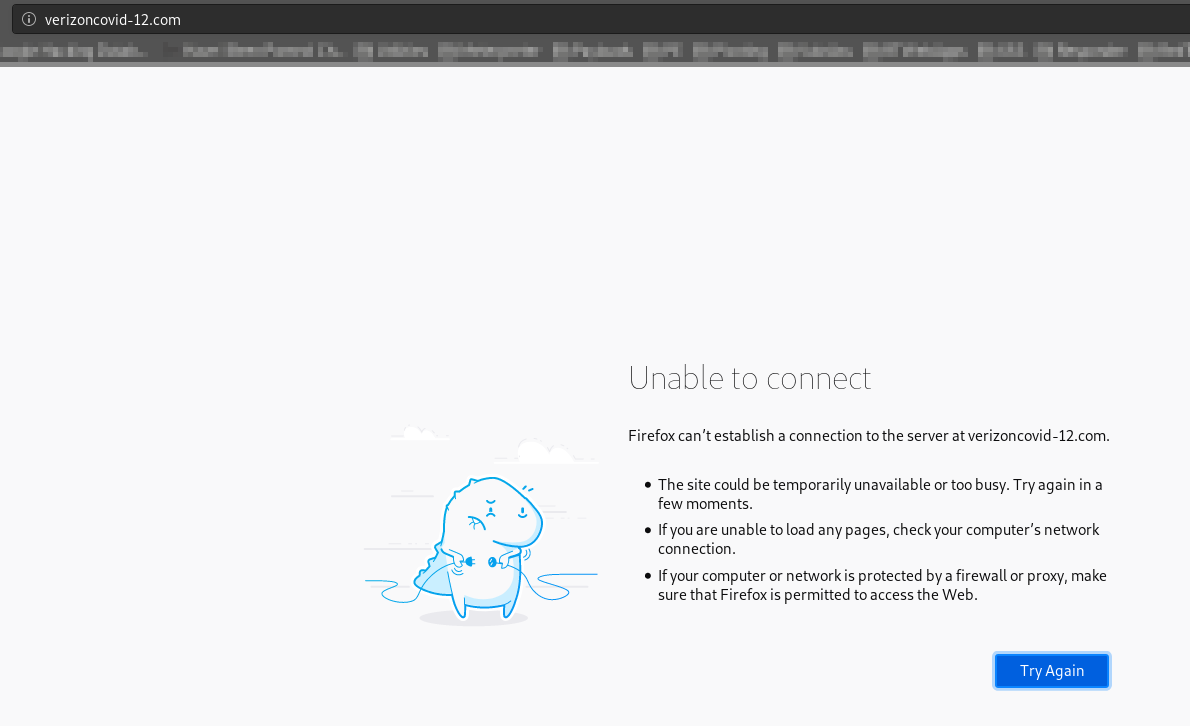
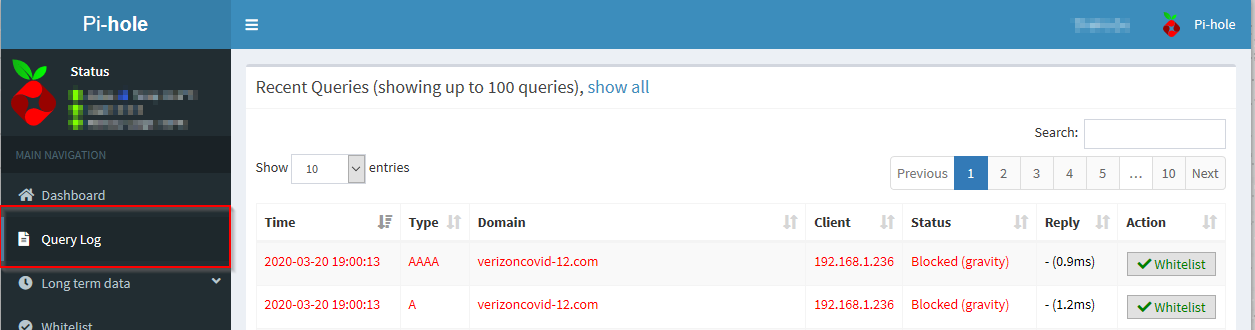
Well done!
Conclusions
This is a home setup scenario. For a small company or test enterprise solutions, we would suggest installing Pi-hole in a docker container and configuring the Domain Controller to point to the Pi-hole as your primary DNS.
To reiterate, we recommend this setup for HOME use only. Hospitals and healthcare providers should use business class solutions for DNS services and protective DNS.




